Frequently Asked Questions in Linux Interviews
In a Linux interview, proficiency in basic commands is crucial. Familiarize yourself with commands such as ls, cd, cp, mv, and grep, as they form the foundation of Linux operations. FAQs provide a glimpse into the breadth of topics that may arise during a Linux interview. Tailor your preparation to cover a wide range of technical and conceptual aspects related to Linux administration and operations.

What is Linux?
Linux is an open-source, Unix-like operating system kernel that serves as the core of various Linux distributions. Developed by Linus Torvalds in 1991, Linux has grown into a robust and highly customizable platform. Its strength lies in its stability, security, and scalability, making it a preferred choice for a wide range of applications, from servers and embedded systems to desktop computers. One of Linux’s defining features is its collaborative development model, with a vast community contributing to its continuous improvement. With a command-line interface and a wealth of powerful tools, Linux empowers users to have precise control over their systems, fostering a rich ecosystem of free and open-source software.
What is the Linux Kernel?
The Linux Kernel is the core component of the Linux operating system, serving as the bridge between hardware and software. Developed by Linus Torvalds and the open-source community, it is the fundamental part of the operating system responsible for managing system resources, such as the CPU, memory, and peripheral devices. The kernel acts as an intermediary, facilitating communication between software applications and the computer’s hardware. Notable for its modular design and efficiency, the Linux Kernel is continually evolving, with regular updates and contributions from developers worldwide. Its open-source nature allows for transparency, collaboration, and customization, making it a key element in the success and adaptability of the Linux operating system across diverse computing environments.
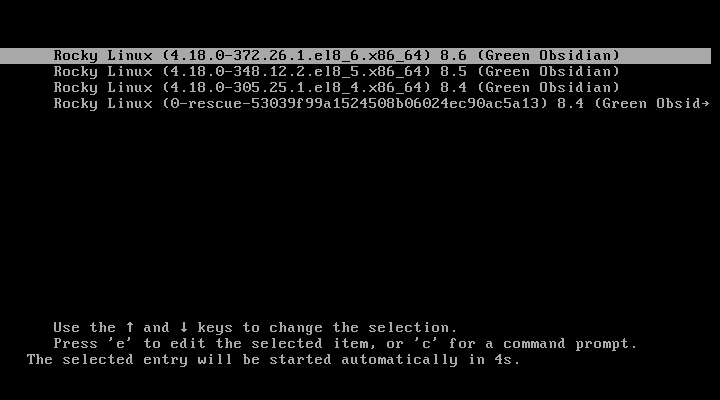
What is GRUB?
GRUB, or the Grand Unified Bootloader, is a widely used bootloader in the Linux and Unix computing environments. Serving as the initial software that loads and manages the operating system during the boot process, GRUB allows users to select from multiple operating systems or kernel configurations on a single device. Developed with flexibility in mind, GRUB supports a variety of filesystems and provides a menu interface for users to choose their desired operating system or kernel at startup. Additionally, GRUB plays a crucial role in the Linux boot process by loading the kernel into memory and initializing the essential components required for the operating system to start functioning. Its open-source nature and widespread adoption make GRUB a vital component for managing the boot process on Linux and other compatible systems.
What are essential components of Linux?
Linux comprises several essential components that work together to form a complete and functional operating system. These components include:
1. Kernel: The core of the operating system, the Linux kernel manages hardware resources, provides essential services, and facilitates communication between software and hardware.
2. Shell: The command-line interface through which users interact with the operating system. It interprets user commands and executes them, allowing users to perform various tasks.
3. Filesystem: Linux uses a hierarchical filesystem structure to organize and store data. Directories, files, and links are essential elements of this structure, providing a systematic way to access and manage information.
4. System Libraries: Collections of pre-compiled functions and routines that applications use to perform common tasks. These libraries streamline development and ensure consistency across different software.
5. System Utilities: Command-line utilities and programs that perform various system management tasks, such as file manipulation, process control, and network configuration.
6. System Daemons: Background processes that run independently, providing specific services such as network management, printing, and system logging.
7. Graphical Server: Manages graphical elements of the user interface, enabling the display of graphical applications and desktop environments.
8. Graphical User Interface (GUI): A visual interface that allows users to interact with the system using graphical elements such as icons, windows, and buttons. Common Linux desktop environments include GNOME, KDE, and Xfce.
9. Device Drivers: Software components that allow the operating system to communicate with and control hardware devices, ensuring proper functionality and compatibility.
10. Shell Scripts: Text files containing sequences of commands that can be executed in sequence, automating repetitive tasks and enhancing system management.
Together, these components create a powerful and versatile operating environment, contributing to Linux’s popularity in various computing domains, from servers and embedded systems to desktop computers.
What are shell used in Linux?
In Linux, the term “shell” refers to the command-line interface that allows users to interact with the operating system. Several shells are available, each offering its unique features and functionalities. Common shells include Bash (Bourne Again SHell), known for its widespread use and powerful scripting capabilities; Zsh (Z Shell), which combines the features of other shells with additional enhancements for user-friendly interactions; and Fish (Friendly Interactive SHell), designed for ease of use with features like auto-suggestions and syntax highlighting. The shell interprets user commands, manages processes, and facilitates script execution, providing users with a flexible and efficient means of controlling and navigating the Linux operating system. Users can choose the shell that best suits their preferences and requirements, contributing to the adaptability and user-friendliness of the Linux environment.
What is Swap Space in Linux?
Swap space in Linux is a designated area on a storage device, typically a hard drive or SSD, that serves as an extension of the system’s physical memory (RAM). When the physical RAM becomes fully utilized, the Linux kernel transfers less frequently used data from RAM to the swap space to free up memory for more active processes. This process prevents system slowdowns and ensures that essential operations can continue. While swap space provides a valuable safety net for handling memory-intensive tasks, it’s crucial to note that excessive swapping can impact system performance. Therefore, proper configuration of swap space, considering factors such as system requirements and workload, is essential to maintaining optimal Linux system performance.
How to Check Linux Memory Utilization?
To check Linux memory utilization, you can use various commands and tools to get detailed information on how your system’s memory is being used. Here are some commonly used methods:
1. Using the free Command:
Open a terminal and type the following command
free -mThis command provides a summary of total, used, and free memory in megabytes.
2. Using the top Command:
Enter the following command in the terminal
topThe top command displays real-time information about system processes, including memory usage. Look for the “KiB Mem” line to see the memory statistics.
3. Checking Memory with htop:
If not installed, you can install htop using your package manager
sudo apt-get install htop # For Debian/Ubuntu
sudo yum install htop # For CentOS/FedoraRun htop in the terminal, and it provides an interactive and visually appealing way to view system stats, including memory usage.
4. Examining /proc/meminfo:
This file contains detailed information about memory usage. Use the following command
cat /proc/meminfoLook for values like MemTotal, MemFree, Buffers, and Cached to understand different aspects of memory utilization.
5. Using vmstat for Virtual Memory Statistics:
Run the following command
vmstat 1The vmstat command provides a snapshot of system statistics, including memory usage, at regular intervals.
6. Checking Swap Usage:
To see swap usage, use the following command
swapon -sThis command shows information about swap space usage.
By employing these commands and tools, you can gain insights into how your Linux system is utilizing memory resources, helping you identify potential issues and optimize performance.
How to Check Linux Disk Space Utilization?
Checking Linux disk space utilization is crucial for managing system resources efficiently. Here are several commands and tools you can use to inspect disk space:
1. Using df Command:
Open a terminal and type
df -hThe df command displays disk space usage on all mounted filesystems. The -h option makes the output human-readable, showing sizes in a more understandable format.
2. Checking Specific Directory Space with du Command:
To check disk usage of a specific directory, use
du -h /path/to/directoryThe du command provides a summary of disk space usage for the specified directory, with the -h option for human-readable sizes.
3. Using lsblk Command:
To display block devices along with their mount points and disk space usage, usev
lsblkThis command provides a hierarchical view of storage devices and their mount points.
4. Checking Disk Space with GParted (Graphical):
If you prefer a graphical tool, you can install GParted
sudo apt-get install gparted # For Debian/Ubuntu
sudo yum install gparted # For CentOS/FedoraRun gparted to launch the graphical partition editor, where you can visually inspect disk usage.
5. Checking File Sizes with ncdu:
Install ncdu using your package manager
sudo apt-get install ncdu # For Debian/Ubuntu
sudo yum install ncdu # For CentOS/FedoraRun ncdu in the terminal to interactively explore and analyze disk space usage.
6. Using Disk Usage Analyzer (Graphical):
Many Linux distributions come with a disk usage analyzer tool. For example, on GNOME-based systems, you can find it in the Applications menu.
By employing these commands and tools, you can effectively monitor disk space utilization, identify space-consuming directories or files, and take necessary actions to manage your Linux system’s storage efficiently.
What are an Inode and PID?
Inode
In a Unix-like file system, an Inode (Index Node) is a data structure that represents a file or directory. Each file or directory is associated with an Inode, and this structure contains metadata about the file or directory, excluding its name and actual data content. Inode information includes details such as file permissions, ownership, timestamps, and pointers to the data blocks on the disk where the actual content is stored. Inodes facilitate efficient file system management, allowing the operating system to organize and access files and directories.
PID (Process ID)
PID stands for Process ID, and it is a unique identifier assigned to each running process on a Unix-like operating system, including Linux. When a program or command is executed, the operating system assigns it a unique numeric identifier known as the PID. The PID allows the system to track and manage processes, facilitating actions such as starting, stopping, or monitoring them. PIDs are essential for process management, enabling the operating system and users to interact with and control running applications and services effectively.
What are Daemons?
In computing, daemons are background processes or services that run on a Unix-like operating system, including Linux, independently of user interactions. These processes typically perform specific tasks, such as handling system requests, managing hardware devices, or providing network services. Daemons run in the background, detached from any terminal, and are often initiated during the system’s boot process. They operate silently, continuously, and persistently, waiting for events or requests to trigger their predefined actions. Daemons play a crucial role in the stability and functionality of a system by handling essential tasks without direct user intervention, allowing users to interact with the system smoothly while these background processes manage various system functions.
What are Process States in Linux?
In Linux, processes undergo various states during their lifecycle, defined by their execution status and activity. The primary process states include:
- Running: The process is actively executing instructions.
- Sleeping (Interruptible): The process is waiting for an event to occur, such as input/output completion, and can be interrupted.
- Sleeping (Uninterruptible): Similar to interruptible sleep, but the process cannot be interrupted, typically associated with waiting for hardware resources.
- Stopped: The process is halted, usually due to receiving a signal or manual intervention.
- Zombie: The process has terminated but retains an entry in the process table, awaiting its parent process to collect exit status.
These states help the operating system manage and track the execution of processes, ensuring efficient resource utilization and system stability.
What is GUI?
GUI, or Graphical User Interface, refers to a visual way of interacting with a computer program or operating system that utilizes graphical elements such as icons, buttons, windows, and menus, rather than relying solely on text-based commands. GUIs aim to enhance user experience by providing an intuitive and user-friendly environment where users can perform tasks using visual representations. This graphical approach simplifies complex interactions, making computers more accessible to a broader audience. GUIs are widely used in modern operating systems, applications, and software, offering an interface that allows users to interact with their devices in a more visually intuitive and efficient manner.
What is CLI?
CLI, or Command Line Interface, is a text-based method of interacting with a computer or software program where users input commands using a keyboard. In a CLI, users communicate with the system by typing specific textual commands, and the system responds with text-based outputs. Unlike Graphical User Interfaces (GUIs), CLIs don’t rely on graphical elements but instead focus on the efficiency of text-based commands. While it may seem less intuitive for some users, CLIs offer powerful control over the system, facilitate automation through scripts, and are often favored by advanced users, system administrators, and programmers for their precision, speed, and resource efficiency.
What is the Root Account?
The root account, often referred to as the superuser or administrator account, is the highest-level user account in a Unix-like operating system, including Linux. This account possesses unrestricted access and privileges, allowing it to execute commands and modify system files and configurations with no limitations. The root account has the authority to perform critical system tasks, install and uninstall software, and make changes that can affect the entire system. Due to its powerful capabilities, users are typically advised to use the root account judiciously to avoid unintended system alterations or security risks. It is common practice to switch to the root account only when necessary and employ regular user accounts for everyday computing tasks to enhance system security.
What is Open Source Software?
Open Source Software refers to computer software whose source code is made available to the public, allowing users to view, modify, and distribute the code freely. This open and transparent approach encourages collaboration, fostering a community-driven development model. Users are not only allowed but also encouraged to contribute improvements, modifications, and enhancements to the software. The philosophy of open source promotes accessibility, adaptability, and collaborative innovation, ensuring that the software remains free and accessible to a global community. Examples of popular open-source software include the Linux operating system, the Apache web server, and the Firefox web browser.
What are the Linux Directory Commands?
Linux provides several commands for navigating and managing directories. Here are some essential directory commands:
pwd(Print Working Directory): Displays the current working directory.
pwdls(List): Lists files and directories in the current directory.
ls- Use with options like
-lfor detailed listing or-ato show hidden files.
cd(Change Directory): Moves to the specified directory.
cd directory_name- Use
cd ..to go up one level.
mkdir(Make Directory): Creates a new directory.
mkdir new_directoryrmdir(Remove Directory): Removes an empty directory.
rmdir directory_to_removecp(Copy): Copies files or directories.
cp source destination- Use the
-roption for recursive copying of directories.
mv(Move): Moves or renames files and directories.
mv source destination- Use for both moving and renaming.
rm(Remove): Deletes files or directories.
rm file_to_remove- Use with caution, and add the
-roption for directories.
find: Searches for files or directories.
find /path/to/search -name filename- A powerful command for locating files based on various criteria.
locate: Finds files and directories quickly using a pre-built index.locate filename- Update the index with
sudo updatedbbefore usinglocate.
- Update the index with
These commands are fundamental for navigating, creating, modifying, and managing directories and files in a Linux environment. Always exercise caution, especially when using commands like rm to avoid unintentional data loss.
What is the Redirection Operator?
The redirection operator in Linux, represented by the greater-than (>) and less-than (<) symbols, enables the manipulation of input and output streams in the command line. The > operator is used for output redirection, allowing the content of a command’s output to be written to a file or device, overwriting its existing content if the file already exists. For example, command > file.txt will redirect the output of “command” to “file.txt.” Conversely, the < operator is employed for input redirection, enabling a command to read input from a file rather than from the standard input (keyboard). Both operators contribute to the flexibility and efficiency of the command line by facilitating the seamless manipulation of data streams in various operations and scenarios.
What are the Different Vim Modes?
Vim, a versatile text editor, operates in different modes, each serving specific purposes to enhance text editing efficiency. The primary modes in Vim are:
- Normal Mode: The default mode for navigating and manipulating text. In this mode, you can move the cursor, delete, copy, and paste text without entering specific commands.
- Insert Mode: Entered by pressing
iin Normal Mode, Insert Mode allows direct text input. Users can type and edit text as they would in a standard text editor. - Visual Mode: Accessed by pressing
vin Normal Mode, Visual Mode enables the selection of text in a character-by-character or line-by-line fashion. Selected text can then be copied, deleted, or manipulated. - Command-Line Mode: Triggered by pressing
:in Normal Mode, Command-Line Mode allows the execution of various commands, such as saving changes, searching, or opening files. - Ex Mode: Accessed by typing
Qin Command-Line Mode, Ex Mode provides an interface for executing complex commands and scripting. It is less commonly used for everyday editing tasks.
Understanding and efficiently transitioning between these modes is fundamental to mastering Vim and leveraging its powerful features for text editing and manipulation.
What is an Alias?
In computing, an alias refers to a user-defined shorthand or alternate name for a command or a series of commands. Users create aliases to simplify and customize their command-line experience, allowing them to execute complex or frequently used commands with a shorter, more memorable name. Aliases are often defined in configuration files like .bashrc or .zshrc on Unix-like systems. For example, an alias could be created to substitute a long command like ls -la with a shorter version, such as ll. This not only reduces typing but also enhances productivity by providing users with a more convenient way to execute common tasks or complex commands. Aliases are prevalent in command-line interfaces, including those of Unix-based operating systems like Linux and macOS.
How to List All Processes Running on a Linux?
To list all processes running on a Linux system, you can use various commands.
psCommand:
ps auxThis command displays a detailed list of all processes running on the system, including their process ID (PID), resource usage, and other information.
topCommand:
topThe top command provides a real-time, interactive view of system processes, updating dynamically. Press q to exit.
Choose the command that best suits your needs, depending on whether you prefer a detailed list, an interactive view, or specific information about processes on your Linux system.
What is a Soft Link?
A soft link, also known as a symbolic link or symlink, is a type of link or pointer in a file system that references another file or directory. Unlike a hard link, which directly points to the inode of the target file or directory, a soft link is a separate file with its own inode that contains the path to the target file or directory. This provides a level of abstraction and allows for more flexibility, as soft links can span different file systems and even reference non-existent files. If the target file or directory is moved or deleted, the soft link remains but becomes broken, pointing to a location that no longer exists. Soft links are created using the ln command with the -s option in Unix-like operating systems. They are commonly used for creating aliases, simplifying file organization, or referencing files and directories across different locations.
What is a Hard Link?
A hard link is a mechanism in a file system that associates multiple file entries with the same inode, which is the data structure that stores information about a file or directory. Unlike symbolic links (soft links), which are separate files that point to a target file, hard links essentially create additional directory entries that point directly to the same data blocks as the original file. All hard links to a file are essentially equivalent; changes to the content of one hard link are reflected in all others because they all share the same inode. Hard links can exist within the same file system, and when the last hard link to a file is removed, the file’s data blocks are only deallocated when all links to the file are deleted. Hard links are created using the ln command in Unix-like operating systems.
What are Hidden Files in Linux?
Hidden files in Linux are files or directories whose names begin with a dot (.). These files are not displayed when you use typical file listing commands like ls without additional options. The convention of using a dot as a prefix is a way to hide configuration files, system files, and other files that are not meant to be directly manipulated by users on a regular basis. Hidden files often store settings or data necessary for the functioning of applications or the system itself. To view hidden files in the terminal, you can use the -a option with the ls command, like this: ls -a. Graphical file managers in Linux typically provide an option to show or hide hidden files, often accessible through a menu or a keyboard shortcut like Ctrl + H. Understanding and managing hidden files is important for system administrators and users who want to delve into system configurations and customize their Linux environment.
What are the Different Types of Permissions in Linux?
In Linux, file and directory permissions are categorized into three types, each specifying the level of access granted to different user groups:
- User (Owner) Permissions:
- Read (
r): Allows the user to view the content of a file or list the contents of a directory. - Write (
w): Permits the user to modify the file’s content or create, delete, and rename files within a directory. - Execute (
x): Grants the user permission to execute a file as a program or access the contents of a directory.
- Group Permissions:
- Read (
r): Enables group members to view the content of a file or list the contents of a directory. - Write (
w): Allows group members to modify the file’s content or create, delete, and rename files within a directory. - Execute (
x): Grants group members permission to execute a file as a program or access the contents of a directory.
- Other (Public) Permissions:
- Read (
r): Permits others (users not in the user or group categories) to view the content of a file or list the contents of a directory. - Write (
w): Allows others to modify the file’s content or create, delete, and rename files within a directory. - Execute (
x): Grants permission to others to execute a file as a program or access the contents of a directory.
Permissions are represented by a series of letters or dashes in Linux file listings. For example, rw-r--r-- indicates read and write permissions for the owner, and read-only permissions for the group and others. Understanding and managing these permissions are crucial for maintaining security and control over file and directory access in a Linux system.
How do Change the Permissions of a File or Directory?
To change the permissions of a file or directory in Linux, you can use the chmod command. The chmod command allows you to modify the read (r), write (w), and execute (x) permissions for the owner, group, and others. Here are some examples:
- To Add or Remove Permissions:
- To add execute permission for the owner:
chmod +x filename - To remove write permission for others:
chmod o-w filename
- Using Numeric Representation:
- To set read, write, and execute permissions for the owner, read and execute for the group, and read-only for others:
chmod 750 filename - The numeric representation corresponds to the sum of permission values: 4 for read, 2 for write, and 1 for execute. So, 7 means read (4) + write (2) + execute (1).
- Symbolic Representation:
- To give read and write permissions to the owner and group:
chmod u+rw, g+rw filename - To remove execute permissions for others:
chmod o-x filename
Remember, you typically need administrative privileges (sudo) to change permissions for files or directories you don’t own. It’s essential to exercise caution when altering permissions, as incorrect settings may impact the functionality or security of the system. Always make sure you understand the implications of the changes you’re making.
What is the Grep Command?
The grep command in Linux is a powerful utility used for searching and pattern matching within text files or command output. Its name is derived from the “Global Regular Expression Print” it originally performed. grep allows users to specify a search pattern using regular expressions, and it then scans one or more files or streams of text for lines that match the pattern, displaying the results to the user. The basic syntax is as follows:
grep 'pattern' filenameHere, ‘pattern’ represents the text or regular expression you want to search for, and filename is the name of the file in which you want to search. Commonly used options with grep include -i for case-insensitive matching, -r for recursive searching in directories, and -n to display line numbers along with matched lines. grep is a versatile tool widely employed for text processing, log analysis, and extracting specific information from large datasets in Unix-like operating systems.














