
Managed Service Providers Should Provide Cloud Services
Managed Service Providers Should Provide Cloud Services Customer expectations are at an all-time high, along with demand for cloud services. A comprehensive cloud solution has never been more difficult to develop because customers demand a wide range of services from a single source. But specifically what must you supply to differentiate yourself from competing managed…
What is Puppet?
What is Puppet? You want to automate as many processes as you can in DevOps. With large infrastructures, manually configuring environments takes weeks. By the time everything is configured, you are putting out fires rather than introducing fresh, practical solutions like Rancher servers. Puppet assists in automating manual processes to swiftly deploy apps and provision…

How Does Workload Automation Work?
How Does Workload Automation Work? Workload automation is used more frequently and has greater advantages as systems become more heterogeneous and complicated. Workload automation is a centralized answer to repetitive, error-prone tasks that helps both the IT team and the company. What is Workload Automation? The process of using software solutions to organize and manage…
What Is a Data Breach and How Does It Occur?
What Is a Data Breach and How Does It Occur? No matter the sector, location, or reputation, data breaches represent a serious danger to businesses of all sizes. A data breach can have a variety of negative effects on a company, from expensive penalties and settlements to long-term brand harm, clientele loss, and, in the…
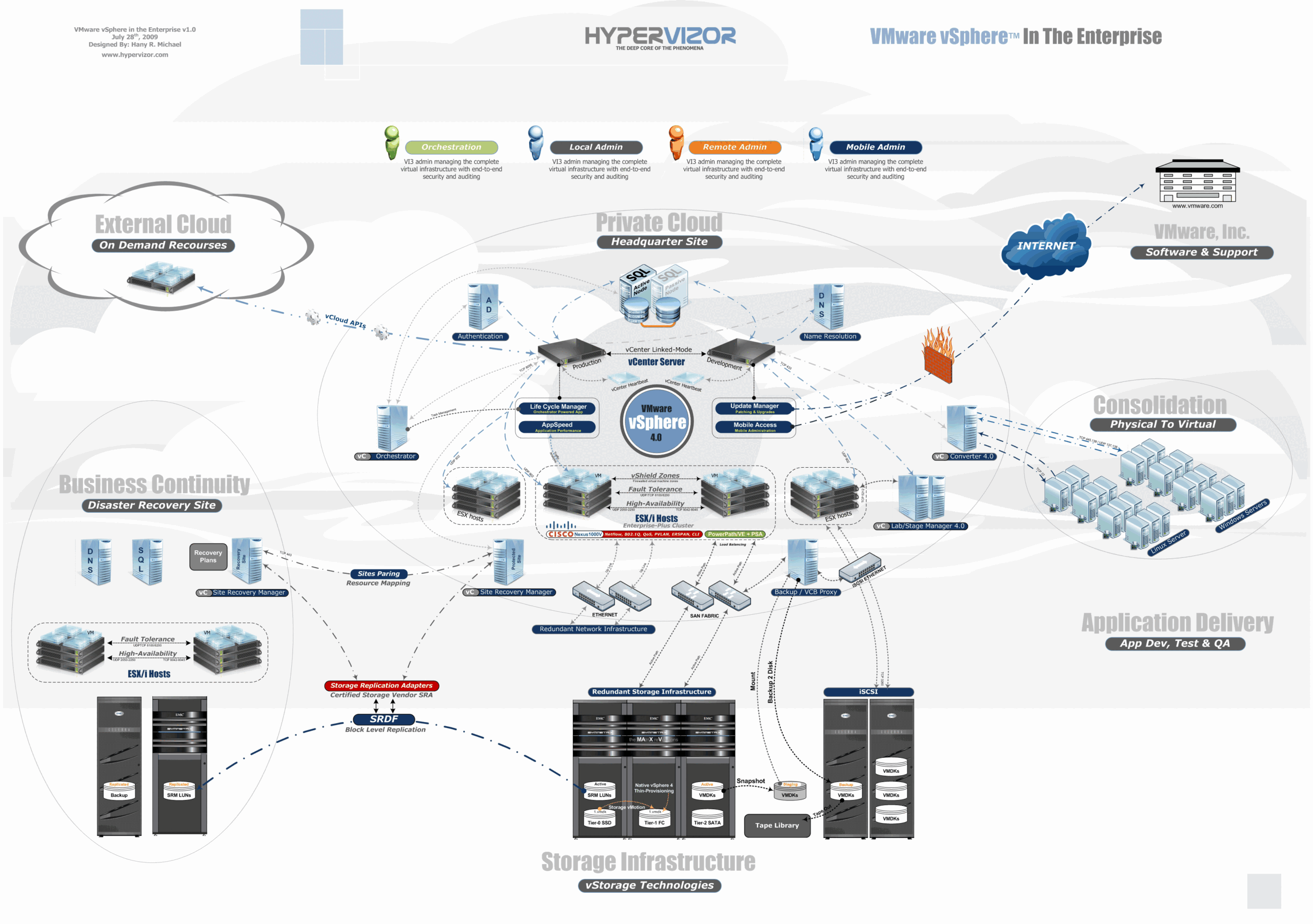
What is a Virtual Data Center?
What is a Virtual Data Center? An on-premise data center can be replaced with a virtual data center since it is more affordable, adaptable, and useful. A virtual data center enables a business to employ cloud-based resources and build scalable infrastructure that perfectly matches operational needs rather than relying on physical hardware. Introductions to virtual…
Backup and Disaster Recovery (BDR)
Backup and Disaster Recovery (BDR) The ability to prepare for future interruptions is a crucial (but sometimes disregarded) component of creating a successful business. Backup and disaster recovery (DR) are essential to company continuity because they help manage incidents that impair operations. Events like data breaches and power outages can result in irreversible data loss,…
Remote Work Security
Remote Work Security The Covid pandemic has compelled companies all around the world to embrace a work-from-home culture. While there are many advantages to this change in work dynamics, it has also highlighted security issues related to remote work. Why Is Remote Work Security Important & What Does It Entail? When employees work remotely, firm…

How to Add a New Disk to Expand the Size of a Linux LVM
How to Add a New Disk to Expand the Size of a Linux LVM The main benefit of LVM over conventional disc partitions is its ability for “dynamic partitions,” which allow us to construct and resize (expand or shrink) LVM volumes dynamically as needed. This article explains how to add a new disc to LVM….

What is Blockchain Technology? How Does Blockchain Operation Work?
What is Blockchain Technology? How Does Blockchain Operation Work? You have likely heard the phrase “blockchain technology” in relation to cryptocurrencies like Bitcoin over the past few years. You may even be curious about the definition of blockchain technology. It appears that blockchain is a platitude, but only in the hypothetical sense, as there is…

Best Tools and Software for Server Monitoring in 2022
Best Tools and Software for Server Monitoring in 2022 The use of cloud technology has made it much easier to set up and manage numerous servers for business and application needs. When it comes to load balancing and disaster recovery, businesses like to have a large number of servers. Tools for server monitoring have grown…