What Is a Data Breach and How Does It Occur?
No matter the sector, location, or reputation, data breaches represent a serious danger to businesses of all sizes. A data breach can have a variety of negative effects on a company, from expensive penalties and settlements to long-term brand harm, clientele loss, and, in the worst situations, business failure.
The purpose of this essay is to provide readers with an introduction to data breaches and the most popular methods used by cybercriminals to access private information. Continue reading to learn what steps you can take to defend your company against breach attempts and to get guidance on how to prevent data breaches.

Definition of a Data Breach
A data breach is a security incident in which protected data is accessed, stolen, copied, or disclosed by an unauthorized individual without the consent or knowledge of the data proprietor. A data leak encompasses both the following situations:
- Sensitive information is accessed by a third party.
- An insider threat (employee, contractor, partner, etc.) gains unauthorized access to or copies data
Any organization, from small and medium-sized businesses to large corporations and governmental bodies, is at risk from data breaches. While criminals may target anyone they believe to be vulnerable, hackers frequently give priority to attacking companies that maintain:
- Information that can be used to identify, contact, or impersonate a person personally.
- Information on a person’s past, present, or potential future physical or mental health (PHI)
- Privileged business information (trade secrets, contracts, customer lists, business plans, emails, meeting recordings, agreements, etc.)
- Intangible assets (designs, patents, source code, blueprints, etc.)
- Fiscal information (invoices, credit card numbers, bank details, tax forms, financial statements, etc.).
What Factors Cause Data Breach?
The most common causes of data breaches are security flaws, protocol errors, or human mistake. According to statistics, malware or hacking accounts for 25% of data breaches, although other significant reasons include:
- Loss of a portable device containing private information (24%)
- A leak from within (12%)
- Accidental data exposure, either as a result of error or carelessness (17.4%)
- File or document loss due to physical theft (11.6%).
- A stationary gadget being stolen or lost (5.4%)
- Fraud with credit cards is 1.4%.
Around 3.2% of data breaches have an undetermined root cause. While some businesses would rather not reveal how their files were breached, others are unsure of the circumstances.
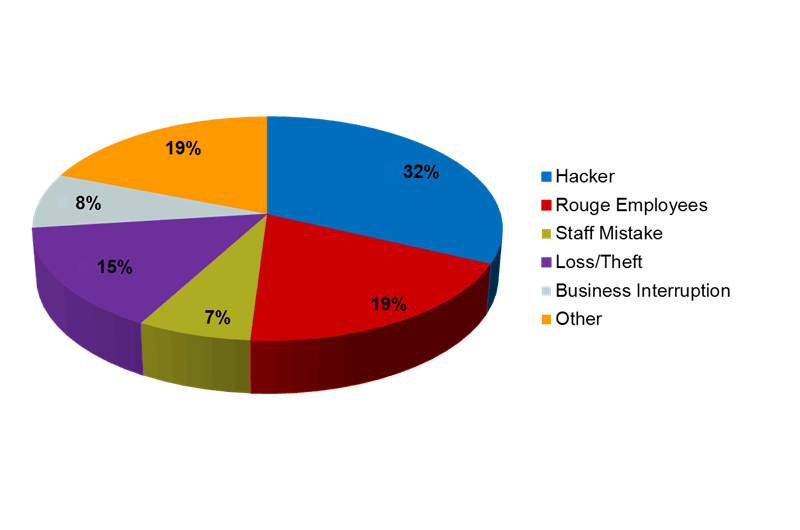
The following are some of the most typical situations that could result in a data breach:
- Weak passwords that make it possible for hackers to guess an employee’s login information.
- A worker clicking on a dangerous email link that brings malware onto a work computer
- An unpatched program that enables backdoor installation on a system by hackers
- By mistake, access privileges were given to the incorrect person.
- A worker misplacing a laptop without at-rest encryption
- A former employee or a dissatisfied insider releasing information with the intention of hurting the business
- A worker reading or editing files on another employee’s computer without authorization.
- An employee using a BYOD device to connect to a risky public Wi-Fi with sensitive data
- A hacker who gained access to an employee account by using credential stuffing and taking advantage of the lack of 2FA
- A bad actor installing malware through a web or app server that has been improperly configured
Methods of Data Breach
A hacker responsible for a data breach can take advantage of a variety of technological lapses and careless user actions. Among the most popular strategies are:
Phishing
Phishing is a social engineering technique used to trick a victim into clicking a dangerous link or disclosing personal information. Phishing attacks most frequently occur over emails, but they can also take place in-person or over the phone to fool staff.
Brute force attacks
Hackers may employ a brute force attack to try and guess the victim’s password from scratch or with the help of information like as the target’s name, work title, family name, pet’s name, etc. Any team concerned with security should prioritize brute force prevention because a top-tier tool can quickly crack a simple password.
Malware
A hacker can establish a persistent access point into the system if they successfully install malware on a firm device or server (for example, through a drive-by download, outdated software, or SQL injection).
Spyware
Spyware is a type of computer program that can stealthily gather data on a person or business and deliver it to the hacker without informing the security staff.
Third-party weaknesses
A hacker may target a third-party partner (such as a colocation or cloud provider) with laxer security procedures even if you successfully secure your local network.
Physical theft
Physical theft is another popular strategy used to obtain data on devices. Opportunistic data breaches frequently include an employee misplacing a device before a laptop, USB drive, or mobile phone containing sensitive information ends up in the wrong hands.
Skimming
At a point of sale (POS) device or website, skimmer programs gather payment card information.
Stages of Data Breach
Although each data breach is a distinct incident, most hacks have a similar structure. The stages of an average data breach that originates from outside the victim’s business are broken down in detail below.
Initial Research
Hackers begin an assault by thoroughly researching the target, unless the breach results from an opportunistic circumstance (such as someone losing a mobile phone or sending an email to the wrong address). In their attempt to learn as much as they can about the business, the crooks frequently:
- Checking network ports for flaws that can be exploited
- Looking at the toolchain of the company and looking for any missing updates.
- Searching for weaknesses in the target’s source code
- Gathering online data on pertinent workers (personal data is useful for cracking passwords and contacts help prepare phishing strategies).
- Determining a worker’s vulnerability to phishing attacks
- Watching regular conduct (online or in person) for protocol errors
- Running a few straightforward assaults to gauge the security team’s reaction time and effectiveness
- Gathering broad information (who reviews emails, how quickly do the replies come, if certain times of month come with more pressure on employees than others, are there any third-party partners, are employees active on social media, etc.).
- Once they are aware of the target’s vulnerabilities, hackers plan their initial access point into the network.
Creating Entry Points
The hacker’s methods and tools at this point are determined by the data the criminal obtained in step one. Most tactics centre on attempting to
- Obtain someone’s login information.
- Malware-infect the system
We can divide this phase of a data breach into two groups depending on the strategy:
- Attacks that use networks
- Social attacks
A hacker uses a flaw in the target’s toolkit or network architecture in a network-based attack. Among the most typical escapades are:
- Injections of SQL
- Firewall flaws.
- Session hijacking
- UPnP shortcomings
- Integrating cloud storage has bugs.
An attacker uses a social attack to deceive a worker into giving them access to the target network. Most social breaches begin with a phishing email that deceives the reader into opening a malware-infected link or attachment; however other social attacks attempt to bring an attacker into the premises.
Establishing a Foothold
Once a hacker has gained access to the target system, they want to:
- Obtain more information about the victim.
- To locate the desired data, navigate laterally through the network.
- Look for chances to have your privileges increased.
Hackers must remain undetected during these activities, which is why the majority of knowledgeable criminals attempt to:
- Strategically modifying the security components of the system
- Starting remote access programs (RATs).
- New system accounts being created.
- By creating distractions, such as a DDoS attack of beginner level, unrelated to the underlying data breach.
Command-and-control (C2) tools are frequently used at this stage as criminals typically try to maintain system control for as long as feasible. To preserve local control, some hackers can, however, employ so-called “living off the land” tactics, which solely rely on already-existing system components.
Once in possession of the system, a hacker’s objective is to find the target data and, if one hasn’t been prepared beforehand, determine the best way to take the files.
Going After Data
The most frequent objective of this stage is data exfiltration, sometimes referred to as data extrusion or exporting. This process is famously challenging to identify since it frequently looks like normal network traffic. Exfiltration by the hacker involved:
- Slowly transfers the target data into a different, secret folder on the computer.
- Files are sent outside of the victim network, usually in small batches to prevent discovery.
As the hacker tries to divert the security team’s focus, distractions based on DDoS are also frequently used during exfiltration. The hacker has successfully stolen files and can now sell them to the highest bidder after the illicit data transfer.
Even after a hacker takes data, it’s not often the victim who learns about the breach. To keep current with the newest files in the situation, the thief frequently tries to install an advanced persistent threat (APT) within the network.
Some hackers look to encrypt sensitive files before requesting a ransom for the decryption key rather than exfiltrating data. Ransomware assaults, which cause these breaches, are some of the most frequent and expensive intrusions a business can experience.
Prevention of Data Breaches
While you cannot prevent hackers from trying to compromise data, you may embrace best practices to make sure they are unsuccessful in their endeavors. Here are some tips for guarding against data breaches:
- To avoid exploits of out-of-current software, keep all devices, systems, and networks up to date with the most recent updates.
- To inform staff members of social engineering techniques and to teach them what to do if they see suspicious activity, hold cyber security awareness training.
- By using intrusion detection systems (IDS), strong firewalls, anti-virus and malware programs, cloud security rules, VPNs, endpoint threat detection, and cyber kill chains, cyber security can be improved.
- Use network segmentation and zero trust security to restrict an intruder’s ability to move freely between internal systems.
- Make sure employees change passphrases frequently and require the use of strong passwords that are specific to each account.
- To ensure that the company can swiftly recover from a breach attempt, create a disaster recovery strategy and deploy data backups.
- Conduct periodical penetration testing and vulnerability assessments to check your system’s resistance to various data breach techniques.
- Ensure data cannot be decrypted even if a hacker gains access to the database by using end-to-end encryption and diligent key management.














